Onesait Platform in Cloud Native Landscape
The huge community and the large number of open source projects around the cloud native paradigm makes it complicated and confusing to know what to use at any given moment.
For this reason, the Cloud Native Computing Foundation (CNCF) has been offering for several years now a map, the Cloud Native Landscape, which shows all the cloud native solutions, many of which are under its umbrella.
The mission of the CNCF is to foster this set of open source projects by helping to provide end-user communities with viable options for building cloud native applications so that organizations can decide how to approach their cloud journey.
The Cloud Native Landscape acts as an umbrella for cloud native technologies that organizations use to build, deploy and run their applications in the cloud native paradigm.
Categories
The landscape uses the following categories:
- App Definition and Development
- Orchestration & Management
- Runtime
- Provisioning
- Observability & Analysis
Following the map proposed by CNCF, we are going to show the technologies used by Onesait Platform, some of them are part of the core of the Platform, such as Kubernetes, while others are optional technologies or supported in the Platform through the teams that operate the Platform (such as Datadog).
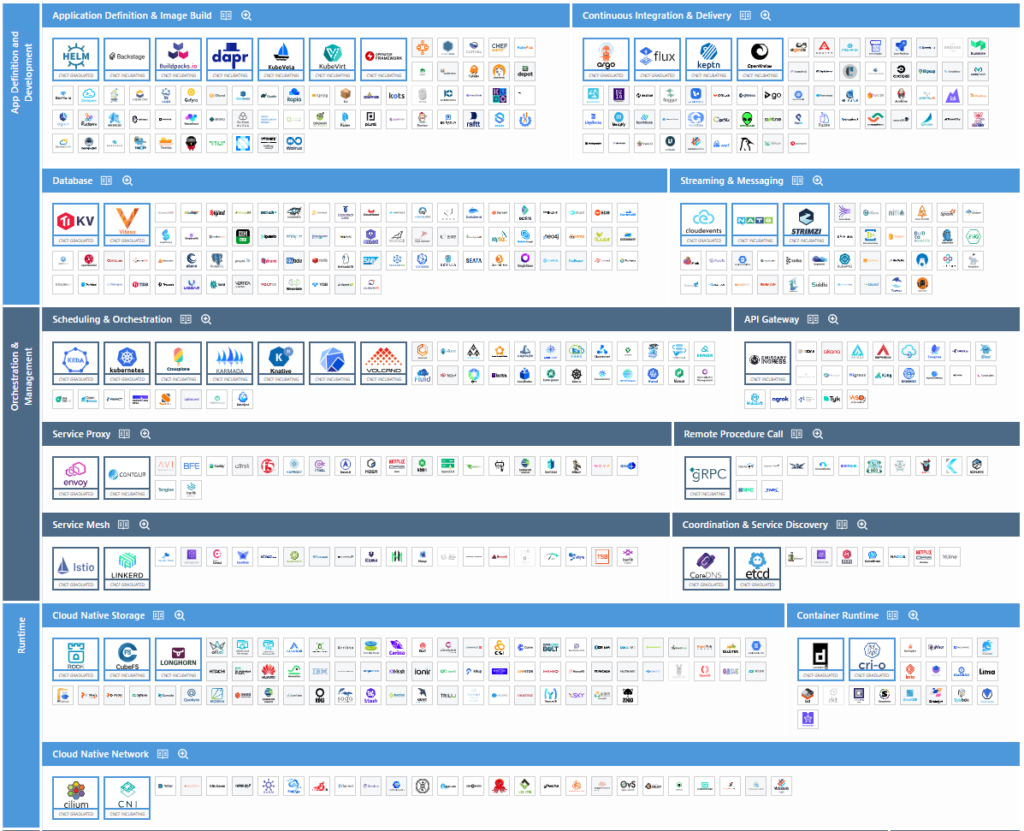
App Definition and Development
This category corresponds to the top layer of the CNCF cloud-native landscape. As the name suggests, the application definition and development layer focuses on the tools that enable engineers to create applications.
Here within we differentiate between the following subcategories.
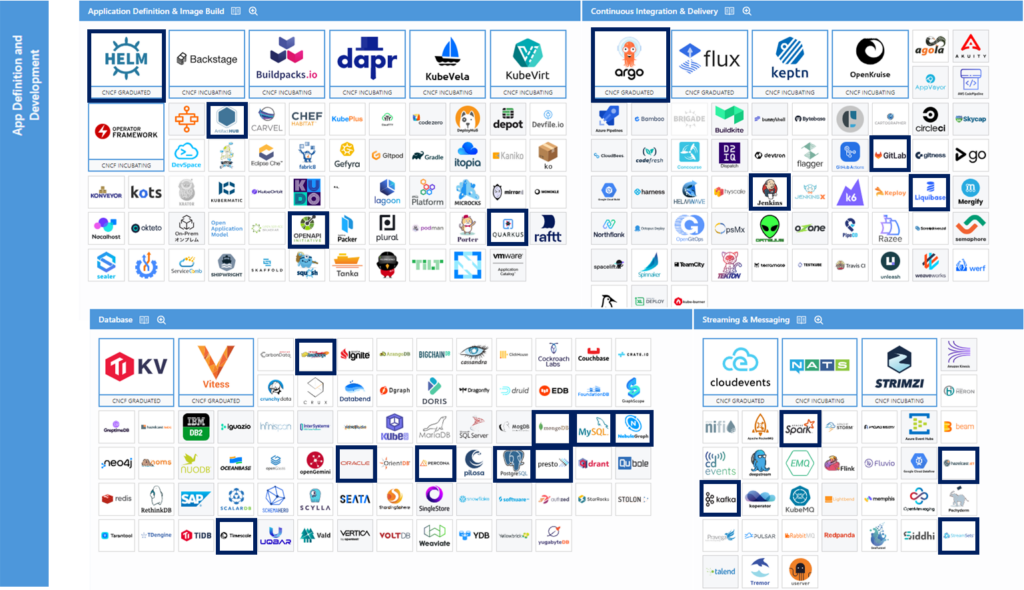
Appication Definition & Image Build
Application definition and imaging is a broad category that can be divided into two main subgroups. First, developer-centric tools that help create application code in containers and/or Kubernetes. Second, operations-centric tools that deploy applications in a standardized way.
Whether you are looking to speed up or simplify the development environment, provide a standardized way to deploy third-party applications, or want to simplify the process of writing a new Kubernetes extension, this category serves as a catch-all for a number of projects and products that optimize the developer and Kubernetes operator experience.
Continuous Integration & Delivery
Continuous integration (CI) and continuous delivery (CD) tools enable fast and efficient development with quality assurance. Continuous integration automates code changes by building and testing the code immediately, ensuring the production of a deployable artifact. CD goes one step further, launching the artifact through the deployment phases.
Mature CI/CD systems watch the source code for changes, automatically build and test the code, and then begin moving it from development to production, where it has to pass a series of tests or validations to determine whether or not the process should continue. The tools in this category enable this integration approach.
Database
A database is an application through which other applications can efficiently store and retrieve data. Databases make it possible to store data, as well as to ensure that only authorized users access it and to allow users to retrieve it through specialized requests. Although there are numerous types of databases with different approaches, ultimately they all have the same general objectives.
Streaming & Messaging
For everything to work properly, the services must communicate with each other and keep each other up to date. To do this, every time a service does something, it sends a message about that particular event.
Streaming and messaging tools enable communication between services by transporting messages (i.e., events) between systems. Each service connects to the messaging service to post events, read messages from other services, or both. This dynamic creates an environment in which individual applications are publishers, i.e., they write events, or subscribers that read events, or more likely both.
Technologies in Onesait Platform
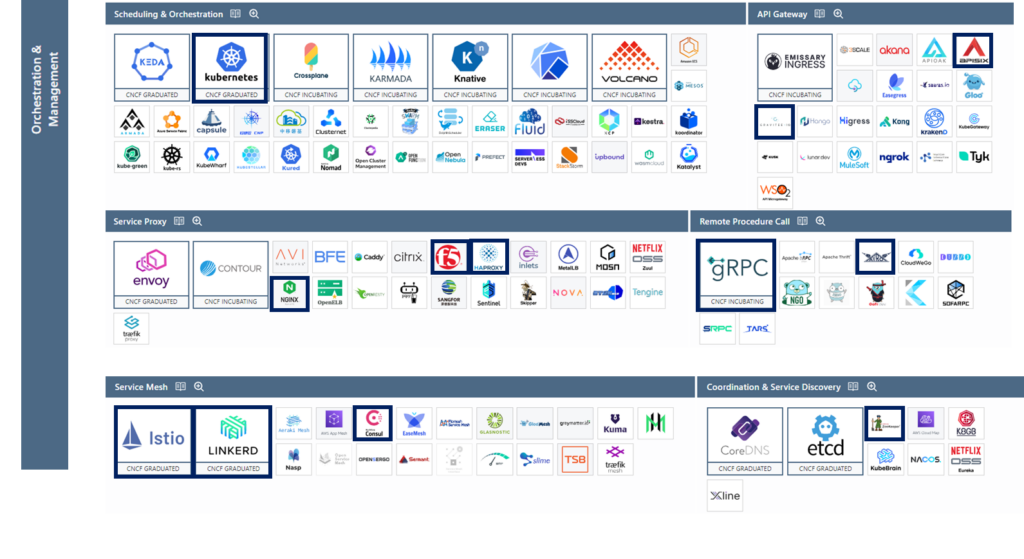
Orchestration & Management
This category ranges from Kubernetes itself, one of the main enablers of cloud-native development, to the infrastructure layers responsible for communication between applications and with the outside world. Inherently scalable, cloud-native applications rely on automation and resiliency, enabled by these tools.
Here we differentiate between the following subcategories:
Scheduling & Orchestration
Orchestration and scheduling refer to the execution and management of containers in a cluster. A cluster is a group of machines, either physical or virtual, connected through a network.
Container orchestrators (and schedulers) are somewhat similar to a computer’s operating system. The operating system manages all applications, runs them and schedules when each application can use hardware resources such as CPU, memory and storage.
One thing that is always present is containers, as their ability to run applications in many different environments is key. Container orchestrators, in most cases Kubernetes, provide the ability to manage these containers. Both containers and Kubernetes are critical to cloud-native architectures.
API Gateway
While we users typically interact with programs through a user interface, such as a web page or desktop application, computers interact with each other through APIs (application programming interfaces). But do not confuse an API with an API gateway.
An API gateway allows organizations to move key functions, such as authorizing or limiting the number of requests between applications, to a centrally managed location. It also functions as a common interface for API consumers (often external).
Service Proxy
A service proxy is a tool that intercepts traffic to or from a given service, applies some logic to it, and then forwards it to another service. Basically, it acts as an intermediary that can collect information about network traffic and apply the rules we have defined to it.
This can be as simple as serving as a load balancer that forwards traffic to individual applications or as complex as an interconnected mesh of proxies that work side by side with applications in individual containers that manage all network connections.
While a service proxy is useful in its own right, especially when directing traffic from the broader network to a Kubernetes cluster, service proxies are also building blocks for other systems, such as API gateways or service meshes, which we’ll discuss next.
Remote Procedure Call
This is a particular technique that allows applications to talk to each other; it is a way of structuring communication between different applications.
Service Mesh
Service meshes manage traffic (i.e. communication) between services. They allow reliability, observability and security features to be added uniformly across all services running in a cluster without requiring code changes.
Along with Kubernetes, service meshes have become some of the most critical infrastructure components of the cloud-native stack.
Coordination & Service Discovery
Modern applications are composed of multiple individual services that need to collaborate to provide value to the end user. To collaborate, they communicate over a network (see cloud-native networks), and to communicate, they must first locate each other. Service discovery is the process of figuring out how to do this.
Technologies in Onesait Platform
Runtime
It covers everything a container needs to run in a cloud-native environment. This includes the code used to start a container, known as the container runtime; tools to make persistent storage available to containers; and those that manage the networking of the container environment.
These resources should not be confused with the networking and storage managed by the provisioning layer, mentioned previously. Those that focus on getting the container platform up and running. The tools in this category are used to start and stop containers, help them store data and allow them to communicate with each other.
The existing subcategories are:
Cloud Native Storage
Storage is where an application’s persistent data is stored, often referred to as a persistent volume. To function reliably, applications need to have easy access to storage. Generally, when we talk about persistent data, we mean storing things like databases, messages, or any other information that we want to make sure doesn’t disappear when an application is restarted.
Container Runtime
A container is a set of computing constraints that are used to run (launch) an application. Containerized applications believe that they are running on their own dedicated computer and do not know that they are sharing resources with other processes (similar to virtual machines).
The container runtime is the software that runs or constrains container applications. The runtime will start an application inside a container and provide it with the necessary resources.
Cloud Native Network
Containers communicate with each other and with the infrastructure layer through a cloud native network. Distributed applications have multiple components that use the network for different purposes. Tools in this category create a virtual network on top of existing networks specifically for applications to communicate, known as an overlay network.
Technologies in Onesait Platform

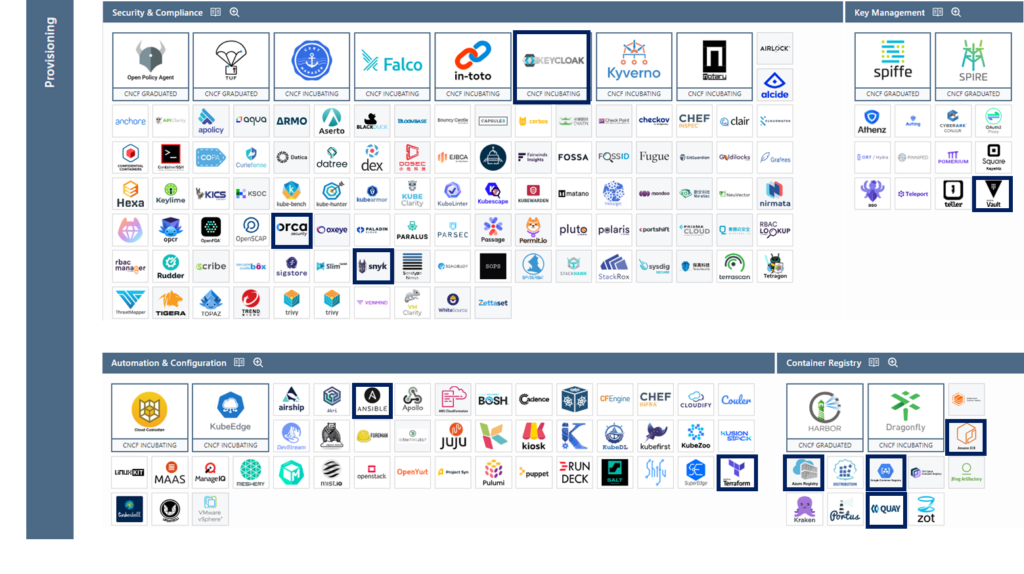
Provisioning
Provisioning is the first layer of the cloud-native environment. It encompasses the tools used to create and enforce the foundation on which cloud-native applications are built. We will find tools to automatically configure, create and manage the infrastructure, as well as to scan, sign and store container images.
The layer also extends to security with tools that enable policy establishment and enforcement, integrated authentication and authorization, and management of secret distribution.
The subcategories found here are:
Security & Compliance
Cloud-native applications are designed to evolve rapidly. To release code on a regular cadence, you need to ensure that the code and operating environment are secure, and accessed only by authorized engineers. The tools and projects in this section provide some of the capabilities needed to build and run modern applications securely.
Key Management
A cryptographic key is a string of characters used to encrypt or sign data. Like a physical key, it locks (encrypts) data so that only someone with the correct key can unlock (decrypt) it.
As applications and operations adapt to a new cloud-native world, security tools are evolving to meet new security needs. Tools and projects in this category range from how to securely store passwords and other secrets (sensitive data such as API keys, encryption keys, etc.) to how to securely remove passwords and secrets from your microservices environment.
Automation & Configuration
Automation and configuration tools speed up the creation and configuration of resources (virtual machines, networks, firewall rules, load balancers, etc.). Tools in this category handle different parts of the provisioning process or attempt to control everything from start to finish. Most offer the ability to integrate with other projects and products in the industry.
Container Registry
Images contain the information needed to run a program (within a container) and are stored in repositories, which in turn are sorted and grouped into registries. Tools that build, run and manage containers need access to these images. Access is provided by referencing the registry (the path to access the container image).
Technologies in Onesait Platform
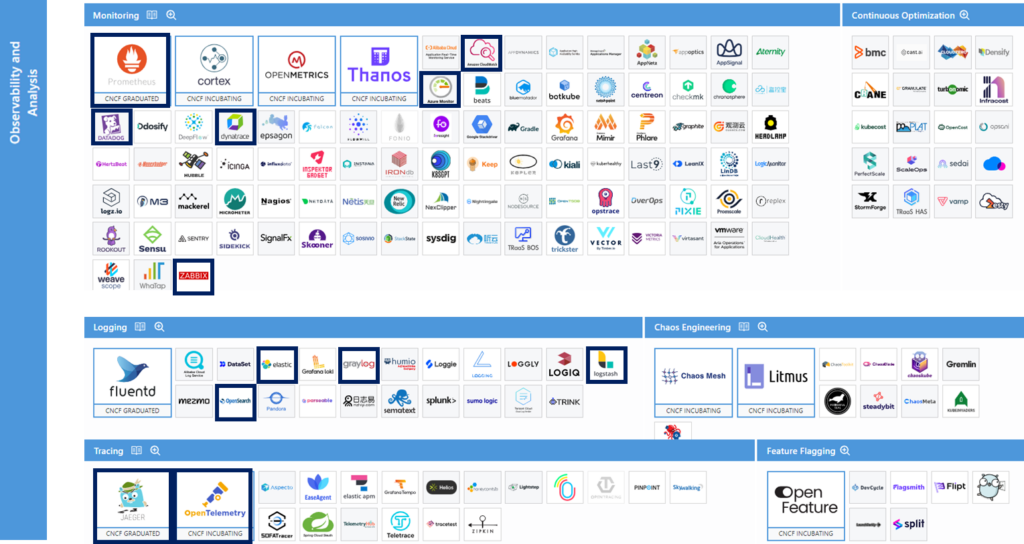
Observability & Analysis
Observability is a characteristic that describes the degree to which a system can be understood from its external results. Measured in CPU time, memory, disk space, latency, errors, etc., computer systems can be more or less observable. Analysis is an activity in which this observable data is examined and made sense of.
To ensure that there are no service interruptions, all aspects of your application will have to be observed and analyzed, so that every anomaly is detected and rectified immediately.
The following subcategories are differentiated:
Monitoring
Monitoring refers to the instrumentation of an application to collect, aggregate and analyze logs and metrics to improve our understanding of its behavior.
While logs describe specific events, metrics are a measure of a system at a given point in time. Monitoring ranges from looking at disk space, CPU usage and memory consumption on individual nodes to performing detailed synthetic transactions to see if a system or application is responding correctly and on time. There are different approaches to monitoring systems and applications.
Continuous Optimization
Continuous optimization is a permanent process of improving systems, processes or products to achieve the highest possible efficiency and performance. We could summarize it as a relentless pursuit of perfection, adapting to new data and perspectives at every moment.
Logging
Applications emit a constant stream of log messages describing what they are doing at any given time. These log messages capture various events occurring in the system, such as failed or successful actions, audit information or health events. Logging tools collect, store and analyze these messages to track error reports and related data.
Along with metrics and traceability, logging is one of the pillars of observability.
Chaos Engineering
Chaos engineering refers to the practice of intentionally introducing faults into a system to test its resilience and ensure that applications and engineering teams are able to withstand problematic and unexpected events. A chaos engineering tool will provide a controlled way to introduce faults and run specific experiments against a particular instance of an application.
Tracing
In a microservices world, services are constantly communicating with each other across the network. Tracing, and a specialized use of logging, allows the path of a request to be traced as it moves through a distributed system.
Feature Flagging
Feature flagging is a software development concept that allows a feature to be enabled or disabled without modifying the source code or having to re-implement it. They are often referred to as feature switches, release switches or feature switches.
Technologies in Onesait Platform